Basic Configuration
Every TypeAuth application requires these fundamental settings:Core Settings
- Name: Unique identifier for your application
- Origin Hostname: The destination where TypeAuth forwards traffic (e.g.,
api.yourcompany.com) - Domain: Your TypeAuth-provided domain for client access
- Format:
api1-{account_slug}-proxy.typeauth.com - Example:
api1-acme-proxy.typeauth.com
- Format:
- Auth ID: Authentication profile ID
Creating an Application
Via Dashboard
- Navigate to Applications
- Click “Create New Application”
- Fill in the required settings
- Save configuration
Via API
Profile Attachments
Applications can be enhanced by attaching various profiles:Available Profiles
-
Authentication Profiles
- API Key validation
- JWT validation settings
- Token Rate limiting
- Expiration
-
Routing Profiles
- URL transformation rules
- Path modifications
- Header management
-
Fraud & Abuse Profiles
- Rate limiting rules
- Threat detection
-
LLM (Language Model) Profiles
- AI content filtering
- Prompt injection protection
- Response validation
-
Schema Validation Profiles
- Upload a OpenAPIv3 schema
- Allow/deny traffic based on that schema
Attaching Profiles
Via Dashboard
- Select your application
- Navigate to desired profile section
- Choose profile to attach
- Save changes
Via API
Application Architecture
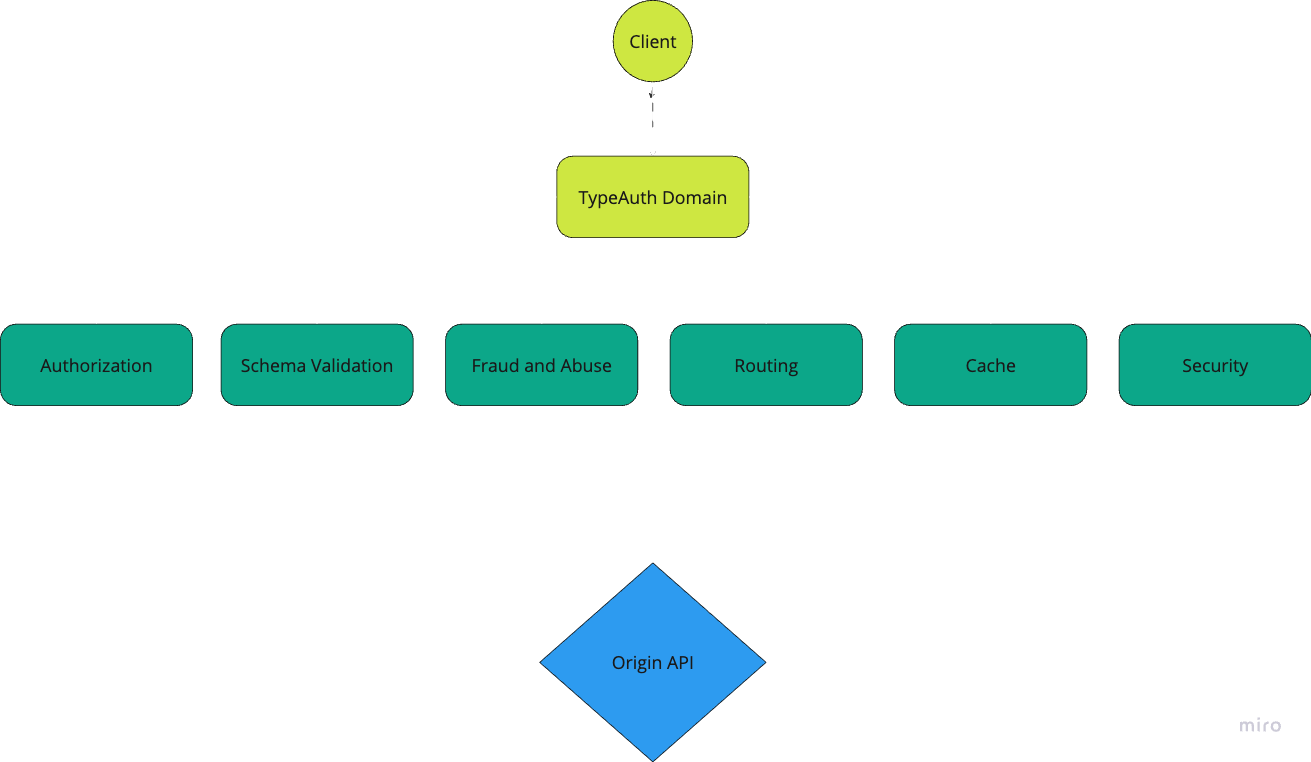
Order of operations
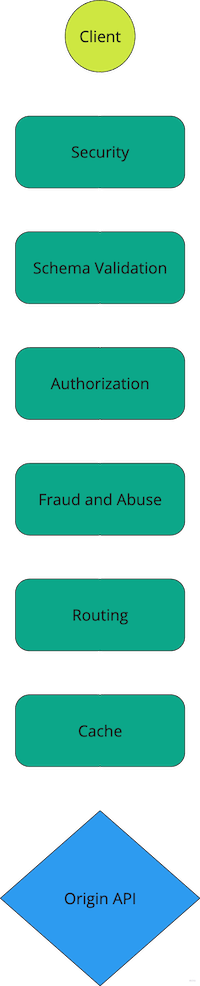
Best Practices
-
Profile Organization
- Create separate profiles for different environments
- Use consistent naming conventions
- Document profile purposes
-
Security
- Always attach authentication profiles
- Configure fraud protection for public APIs
- Regularly review security settings
-
Maintenance
- Regularly review attached profiles
- Remove unused profile attachments
- Keep profile configurations up to date
Monitoring
- Traffic Overview: Monitor request patterns
- Profile Performance: Track profile effectiveness
- Error Rates: Monitor rejection rates
- Latency Impact: Track processing overhead
Limitations
- Maximum 50 applications per account
- Up to 3 tags per application
- One profile of each type per application
- Domain name character limit: 40